
You should always think twice before granting permission to any app on your mobile device. Apps on your mobile device may use your personal information for malicious purposes and share it with content providers. According to Broadcom research, over 10,573 malicious mobile apps were blocked per day in 2018. You should change your phone’s security settings if you want to be safe online. This includes disabling auto-update apps, turning off location services, and restricting access to your personal information.
You should understand what kind of data the app needs, how it uses that data, and whether or not you trust the app developer with this information.
Fortunately, with a little bit of knowledge, you can change your phone’s settings manually. Here, we explain how to get started.
What are app permissions?
Android system permissions are categorized into data and device types. Data permissions include sharing data over the internet. Device permissions include accessing your contacts, phone calls, photos, and other sensitive information. Device permissions are the ones that give the user control over the phone, which categorizes each of them as a highly dangerous permission type. This includes accessing personal information such as call logs, text messages, photos, contacts, etc. The user must be aware of what the app does with this data, and if there is any chance of misuse. Apps that require these permissions should come from a trustworthy source.
Be careful when granting permissions to apps. To access information like your location or contact list or use features like your camera and microphone, apps need your permission to access them. You may be asked for permission when you first download an app, or when the app first attempts to access that information or functionality. For example, does the app really need to access your phone’s exact location or take pictures to do its job?
Install Apps Only From The Official App Store
Here are some things you can do to better secure your privacy when you need to install an app for your private or business purpose.
Download and install apps only through official app stores, such as a device’s manufacturer app store (like Samsung) or operating system app store (Google, Apple). Installing apps from other sources, outside of the official apps store, will expose your smartphone to malicious apps that will surely put your device security at risk.
Before downloading an app, read its privacy policy to see how its data will be used or shared. Will the policy be clear about how the app will use your personal data? If you’re uncomfortable with how your information could potentially be shared, you may want to consider finding an alternative app.
You should be careful when downloading and installing free apps that were recommended by untrusted sites or people, even if they are from the official apps store. There are many apps that do their job as they state, but their intention is to collect and share as much data as they can.
In May 2015, Google removed more than 200 apps from the Play Store after researchers found that the apps had been using the microphone on users’ phones without consent.
App Permissions to Avoid
You should avoid app permissions that are unnecessary for an app to work properly. If the app won’t install when you deny unnecessary permission then you should look for an alternative. For example, if a PDF reader app requests permission to storage (legitimate request) to read PDF files but also requests access to your contacts list (unnecessary) without the option to deny it (otherwise it won’t be installed), then you should completely uninstall it and look for another PDF reader app with storage read-only permission.
A good practice to find a secure app is to check it is installed without giving any permission. It won’t do anything because it has no permission. Then you can start using allowing only the types of permission requests you find serve you best. You can later remove the given permission if you don’t need to use it in the coming future.
How to Manage App Permissions on Android 12?
You can go to your settings to review which apps have access permission to your personal information and which ones don’t. Turn off unnecessary permissions so you don’t accidentally share If you don’t want to give an app permission to access your current location, contacts, photos, etc., consider deleting it. Some apps request too many permissions that aren’t needed for the app’s function. Be especially careful with apps that have access to sensitive information such as your contacts, microphone, camera, storage, and location.
if you don’t know which permissions an app requires, you can check its permissions settings. It contains all the information about the app, including the name of the permissions required by the app.
To manage app permission on Android 12 devices, you can choose both ways:
- Open ‘Settings’, then ‘Apps’, then select the desired app, and then finally select ‘Permissions’.
- On the screen, tap long on the desired app’s icon, then on the upper right corner of the popup menu tap on (i) to open the ‘App Info’ page, and then finally select ‘Permissions’.
Under the ‘Permissions’ label, you can find the already given permissions for your selected app.
When tapping on the ‘Permissions’ label, you’ll be given 3 options to choose from to manage each app permission.
1. Allow app permission only while using the App
Allow this permission type only while using the app. It is one-time permission (until you decide to change it) Allow it when the requested permission is essential to the app functionality, and it is one of the reasons why you’re using this app. You should select this option when you use this app frequently. Allowing app permission only while using the app prevents the app from using that permission in the background when you don’t need it.
2. Ask every time
When setting the app to ask your permission every time it needs access to one of the phone resources, you will be alerted by a popup request to specifically allow that permission. Make sure that this popup request is following your action only and not initiated by the app itself. You should use this method to force an app to ask your permission when you use that app occasionally or when the requested permission type is highly sensitive, like giving access to your microphone.
3. Don’t allow
Select the ‘Don’t allow’ option when a usable app of yours asks (unconditionally) for permission to access one of the phone’s resources that you don’t need to use. In case you’ll do choose to use that denied resource then you’ll get a notification that it is not permitted with redirection to change the permission in the setting. The point is that you will be alerted with a message that you choose that permission.
What App Permissions Should I Allow?
Each app requests different permissions to deliver its features. However, some apps require more than others. For example, a social media app might request access to your contacts, microphone, and camera, but a music player app would likely need access to your phone’s storage space only. You should always ask yourself why and for what you downloaded and installed an app and thus allow permissions that match your needs and void permissions that do not match them.
Best Practice For App Permissions, Real Example
Here is a real example of how to manage securely the Whatsapp app permissions. The Whatsapp app is a good example of how to manage permissions due to its popularity (billiards of phones) as the top social network app, and the variety of permissions that the apps can potentially use (actually, almost everything).
To find out the status of the Whatsapp app permissions (or any other app), on the home screen, tap long on its icon, and on the popup menu tap on (I) (top right) to open the ‘App Info’ page, and then select ‘Permissions’.
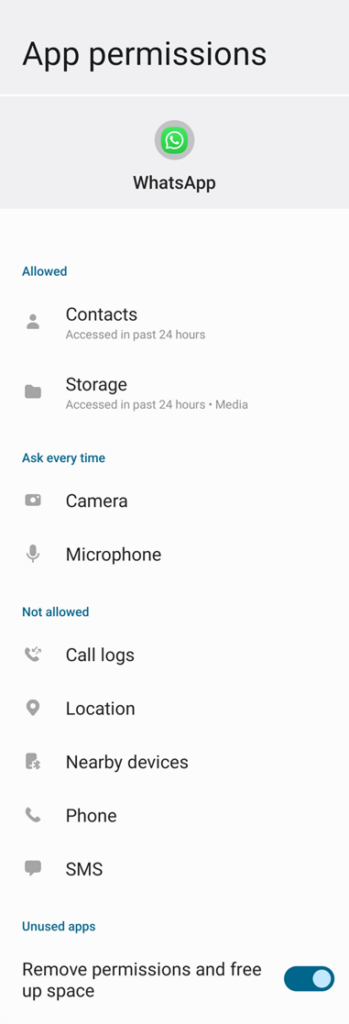
As you can see from the ‘App permissions’ page, the Whatsapp app can potentially access multiple important resources on your devices once you enable those permissions. You will be asked to enable those permissions, but you don’t have to enable each type of permission request unless you really need it.
Here are my recommendations, following my use case of Whatsapp, on how to securely manage its permissions in a way that let me text instantly with my partners, and leave me the option to record a voice message, and share an image only when needed.
Allowed
I use Whatsapp mostly to text with my partners, so I allow Whatsapp permissions to access my Contacts and device’s internal storage only. My Contacts list is required to identify each sent and received message, and the Storage access is used to store messages and upload documents or media files.
Ask every time
The microphone and camera are the most important and sensitive resources of my smartphone (and any other smartphone owner’s) and as such, I do not allow any app to access them by default. I actually force Whatsapp (the same as other apps) to ask for permission every time it has to access them. With this restriction, I can make sure that whatever I say (microphone) and do (camera) is not being recorded without my permission.
Not allowed
The rest of the permissions types that Whatsapp could ask to access are not allowed. I do not allow these permissions for the simple reason that I do not use Whatsapp’s features that need access to these resources. The location permission is a good example of a sensitive resource that should not be allowed on Whatsapp or any other social network app since it could potentially share your precise location (GPS), and approximate location (WiFi networks) with many untrusted people and businesses. Google Maps and Waze, are good examples of apps that you should grant with the location permission because finding your location can help you with your mission.
In case you choose to allow one of the Not-allowed permission then you’ll be notified to change the settings of that app permission.
Unused apps
Turn ON the ‘Remove permissions and free up space’ option to remove permissions of unused apps to free up your device resources. If you don’t plan to use them then simply uninstall them.
Android App Permission Manager
Android 12 Privacy page lists the most used permissions and how many apps have used each of them. It also gives you the option to control and set alerts for the most crucial resources of the phone, which are the camera, microphone, and clipboard.
To display the main Privacy page go to privacy settings:
Settings > Privacy

On top, you’ll find the ‘Permissions used in the last 24 hours’ that list the top types of permissions that were used during the last day. This page example shows that 2 apps used the Camera, 1 app used the Microphone and 4 apps had access to the device’s location.
Click on Camera for example, and you’ll find that the main Camera app and the Signal app were using it and at what exact time.

Another click on the Signal app will show the selected option for the Camera permission (as shown above in the Whatsapp app example).
How to Find Your Device’s Permissions’ Usage History
Android 12 provides a simple one-page to view all of your device’s permissions and check what apps can use them and their usage history. The device’s permissions can be viewed either from the ‘Permissions’ tab or the ‘Apps’ tab.
> List all permissions types and their usable apps history
Use the ‘Permissions’ tab to list all permissions and their eligible apps usage history.
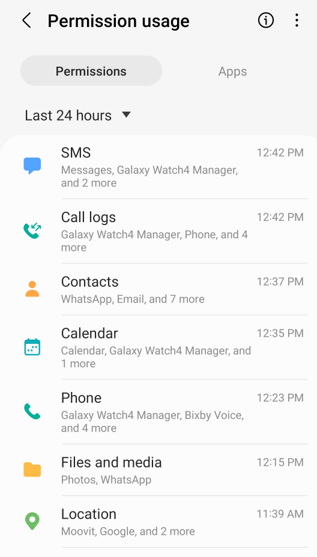
Here you can verify that permissions types are given only to trusted apps that must have them. Disable apps’ permissions that you unintentionally enabled (while installing apps people tend to approve most requests), or you decide now that they should not use them anymore.
The ‘Contacts’ permission, in this example, is given to ‘WhatsApp, Email, and 7 more apps. According to this view, I find that there are many apps that share my private and business contacts list. I should then verify that my contacts list is not being shared with any of those apps’ users.
List all apps and their eligible permissions history.
Use the ‘Apps’ tab to list all installed apps and the permissions that they were granted to use. This view can give you an idea of each mobile app’s security risks.
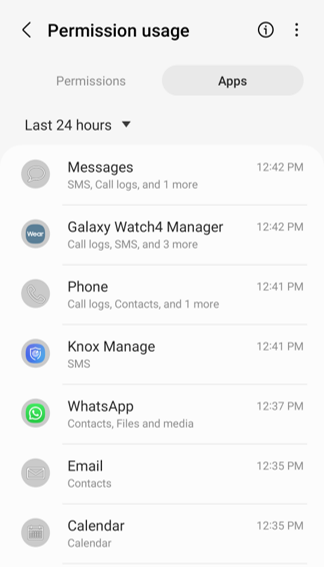
Here you can verify, in a simple page-view, that the given permissions of each app are matching your intent for which you installed that app. As I showed above, with the Whatsapp example, I can see here clearly that it can access the ‘Contacts’ and internal storage only, matching my privacy policy. It can also help you to clear out unnecessary permissions that do not match your privacy policy.
Protect Your Phone From Your Apps
Managing your app’s permissions with caution will increase your privacy and add a great layer of security to your Android device.
IronTel Mobile is the best secure phone of 2022 for business people that really care about their privacy and their business confidential data. IronTel Mobile protects the device from installing malicious apps, injecting spyware, manipulating the OS file system, and compromising the device.
IronTel Mobile is using the newest and most advanced Samsung devices (Galaxy S22 series). It operates Samsung Knox, a multilayer mobile security system, safeguarding the device in real-time starting from booting the device, through the apps’ loading process, and while using apps on regular basis.
The Knox mobile security system provides the best protection for business confidential data. It virtually splits the device into two phones, ‘Personal’ and ‘Work’. You can manage your apps’ permissions on the ‘Personal’ side without affecting the apps on the ‘Work’. The apps on the ‘Work’ side are used for business purposes only with a restricted permission security policy. For example, a ‘Personal’ app with permission to access internal storage, cannot read or write files on the separated and isolated internal storage on the ‘Work’ side.
IronTel Mobile is using also Harmony Mobile (from Check Point ), the best security app for businesses. The Harmony Mobile app blocks malicious app installation, dangerous app permissions, and suspicious app activities. Harmony Mobile scans all links (SMS, emails, social network, web surfing) to prevent downloading and activating cyber attacks from remote sites.
Check out IronTel Mobile’s secure and encrypted business devices.

IRONTEL MOBILE – S24/S24plus/S24ultra
Select IronTel Mobile Device Model: Galaxy S24 Ultra
IRONTEL-MOBILE is built on the advanced Samsung Galaxy S24 Ultra device. [Spec]
Subscribe


